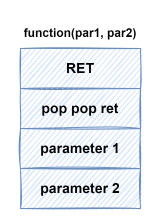
ROP
A class of Code Reuse Attack
- Works by overwriting stack with multiple return addresses
- Chain multiple short pieces of existing code (called ROP gadgets)
- Each ROP gadget ends with the return (ret) instruction
실행 불가능한 메모리와 코드 사이 보안 방어가 존재하는 경우에 공격자가 코드를 실행할 수 있게 하는 컴퓨터 보안 취약점 공격
For binaries of a reasonably large size (think about shared library code) which guarantees amble number of ROP gadgets making to achieve Turing completeness, the attacker can basically compute anything.
We can generalize this attack to indirect control flow transfer instruction.
ROP Notion
ACM CCS 2007
By shifting the reading position, the attacker can interpret the bytes as completely different instructions, potentially exploiting the system.
Original instructions:
If an attacker starts reading one byte later, they get:
ROP(Return Oriented Programming)
Return Oriented Programming은 기본적으로 RTL 기법과 Gadget을 이용해서 공격에 필요한 코드를 프로그래밍하는 기법입니다.라이브러리의 함수들을 사용하기 때문에 DEP/NX 방어 기법을 우회할 수 있고 사용하고 있는 함수의 got 값을 출력하고
https://velog.io/@silvergun8291/ROPReturn-Oriented-Programming

 Seonglae Cho
Seonglae Cho